Automated AWS Deployment
The purpose of this guide is to enable seamless deployment and configuration of Alert Logic Managed Detection and Response (MDR) in an AWS account while taking full advantage of Alert Logic and AWS automation.
This guide helps you understand how Alert Logic interacts with AWS resources by providing a reference deployment architecture. It then outlines the steps required to automate deployment of that architecture. An alternative automated deployment architecture is available using AWS Control Tower.
To automate Alert Logic deployment in AWS , you must use both Alert Logic and AWS automation tools. This document outlines the complete process:
- Retrieve Alert Logic IAM policy
- Create IAM policy and third-party role using AWS Cloud Formation
- Provide Alert Logic the third-party role
- Create an Alert Logic deployment
- Automatic deployment of AWS protection
After you complete this process, your AWS account will be fully protected by the Alert Logic MDR platform.
Supported subscription types
- Managed Detection and Response Essentials
- Managed Detection and Response Professional
Deployment architecture
The Alert Logic deployment architecture in AWS provides three levels of service:
- Asset discovery and continuous security protection
- Vulnerability scanning
- Network traffic and log analysis
Automating deployment of Alert Logic in AWS uses services and integrations in each protected AWS account. All interactions with AWS services follow best practices, such as minimum privilege delegation, use of third-party IAM roles, and strong encryption.
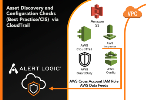
Asset discovery
Click image to expand
Alert Logic provides robust tools to automate the deployment process, and these tools enable a fully automated, hands-off deployment of Alert Logic in AWS. Alert Logic develops and maintains a real-time asset model of your AWS resources such as instances, containers, and security groups.
Automated protection of an AWS account requires integration with the following AWS services:
- AWS IAM—Create a third party IAM role delegating permission to Alert Logic
- AWS CloudTrail—Create a Cloud Trail audit source, used to monitor changes to the environment
- AWS S3, SNS, SQS—Retrieve Cloud Trail log updates
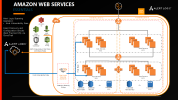
Alert Logic MDR Essentials
Click image to expand
Alert Logic Essentials protection can be applied to individual VPCs, and it includes configuration auditing for common AWS security issues and host-based vulnerability scanning. In addition to the requirements for Asset Discovery, an EC2 instance is used to perform the vulnerability scanning.
The Alert Logic automation selects the most cost-effective scanning appliance for your environment and automatically shuts it down when there are no hosts to be scanned. This automation results in low overhead for providing security evaluation in your network.
Automated protection of an AWS VPC with Essentials requires integration with the following AWS services:
- AWS EC2—Alert Logic scanning appliance
- AWS VPC— Security groups, route tables, and network ACLs to allow communication with Alert Logic and between the scanning appliance and target hosts
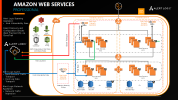
Alert Logic MDR Professional
Click image to expand
Alert Logic Professional protection can be applied to individual VPCs and includes all features of Essentials, plus log collection, integration with AWS GuardDuty, and network traffic analysis.
Automated protection of an AWS VPC with Professional requires integration with the following AWS services:
- AWS EC2—Alert Logic IDS appliance
- AWS VPC—Security groups, route tables, and network ACLs to allow communication with Alert Logic and between the IDS appliance and protected hosts
- AWS GuardDuty, AWS Config, AWS VPC Flow Logs—To configure protection of this account with AWS GuardDuty and provide security findings to Alert Logic
Deployment automation in AWS and Alert Logic
To protect an AWS account, you must create a deployment in the Alert Logic MDR platform. This deployment object references to AWS IAM policies used to interact with your environment and serves as the primary container for the assets contained in that AWS account. Automating deployment requires the following steps, each of which can be automated.
Retrieve IAM policy
Use the Alert Logic CLI to retrieve the latest full deployment policy for AWS. For details on other options, like minimal permission and policies for manual deployment, consult the Cloud Policies (themis) service reference.
alcli themis get_role --account_id 12345678 --platform_type aws --role_type ci_full --role_version latestThis command returns a JSON document including:
| aws_account_id | The Alert Logic account ID to establish a third-party trust relationship with |
| cft | References to download a Cloud Formation template that creates an IAM policy and third-party role as described here |
| external_id | Identifier used in the role to prevent confused deputy attacks from reusing this role for any other purpose |
| policy_document | IAM policy to be created |
Sample response:
{
"aws_account_id": "733251395267",
"cft": {
"s3_bucket": "alertlogic-cloud-formation-templates-733251395267",
"s3_key": "ci_full/2020-01-10",
"s3_url": "https://alertlogic-cloud-formation-templates-733251395267.s3.amazonaws.com/ci_full/2020-01-10"
},
"external_id": "12345678",
"platform_type": "aws",
"policy_document": {
"Statement": [
{
"Action": [
"autoscaling:Describe*",
"cloudformation:DescribeStack*",
"cloudformation:GetTemplate",
"cloudformation:ListStack*",
"cloudfront:Get*",
"cloudfront:List*",
"cloudwatch:Describe*",
"config:DeliverConfigSnapshot",
[…]
"Action": [
"iam:CreateServiceLinkedRole"
],
"Effect": "Allow",
"Resource": "arn:aws:iam::*:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling*",
"Sid": "EnableCreationOfServiceLinkedRoleForAutoscaling"
}
],
"Version": "2012-10-17"
},
"type": "ci_full",
"version": "2020-01-10"
} Create IAM policy and third-party role using AWS CloudFormation
The simplest way to create the IAM policy and role is using the AWS Cloud Formation CLI; however, this task can be automated with many tools, including directly creating resources with the AWS CLI or using tools like Terraform. You can also use the AWS Console directly.
Run the following command to create the IAM policy and role:
aws --region us-east-1 cloudformation create-stack --stack-name "mystack" --template-url https://alertlogic-cloud-formation-templates-733251395267.s3.amazonaws.com/ci_full/2020-01-10Sample output:
{
"StackId": "arn:aws:cloudformation:us-east-1:123456789012:stack/myteststack/466df9e0-0dff-08e3-8e2f-5088487c4896"
}Using the CLI, describe the stack and retrieve the IAMRole output key:
}
aws cloudformation describe-stacks --stack-name myteststack
{ Sample output:
"Stacks": [
{
[…]
"Outputs": [
{
"Description": "IAM role",
"OutputKey": "IAMRole",
"OutputValue": "myteststack-iamrole-jsfai1zie2w"
}
],
[…]
] The value of IAMRole will be used to create the credentials in the next step.
Provide Alert Logic the third-party role
Use the Alert Logic CLI to save the Amazon resource of the role that was created. For more information, see the Credential Storage Service.
Run the following command to store the IAM role ARN:
alcli credentials create_credential --account_id 12345678 --name "IAM policy" --secrets '{ "arn": "arn:aws:iam::123412341234:role/alertlogic-iam-role-ci-full", "type": "aws_iam_role" }'Sample output:
{
"created": {
"at": 1592170189,
"by": "0CC0ED48-22EA-407F-A6AA-89D802129067"
},
"id": "6D85344C-660D-418E-9514-D248D558E7A8",
"name": "IAM Policy",
"secrets": {
"arn": "arn:aws:iam::123412341234:role/alertlogic-iam-role-ci-full",
"external_id": "12345678",
"type": "aws_iam_role"
}
} The IAM policy credential is identified by the id field, which will be used in the next step.
Create an Alert Logic deployment
Use the Alert Logic CLI to create a deployment record. This record describes the AWS account that will be protected and will include:
- Human-readable name
- Reference to the credential for the IAM role created in the previous step
- Scope of protection: all VPCs in region us-east-1, with Alert Logic Professional
- Deployment mode, “automatic” indicating that Alert Logic will automatically install Cloud Trail and appliances as detailed in the architecture above
For details on other options, such as manual deployment modes, see the Deployments service reference.
Run the following command:
alcli deployments create_deployment --account_id 12345678 --name "My Deployment" --credentials '{"id": “3009DAAC-BEDF-4663-9A9D-EF19FDBEA964”, "purpose": "discover"}' --mode automatic --scope '{"exclude": [], "include": "key": "/aws/us-east-1", "policy": { "id": "D12D5E67-166C-474F-87AA-6F86FC9FB9BC" }, "type": "region" }'Sample output:
{
"account_id": "12345678",
"cloud_defender": {
"enabled": false,
"location_id": "defender-us-ashburn"
},
"created": {
"at": 1592170376,
"by": "6D85344C-660D-418E-9514-D248D558E7A8"
},
"credentials": [
{
"id": "3009DAAC-BEDF-4663-9A9D-EF19FDBEA964",
"purpose": "discover",
"version": "2020-01-10"
}
],
"discover": true,
"enabled": true,
"id": "2D7DA803-6C82-4C14-8604-7392F2D4E53D",
"mode": "automatic",
"modified": {
"at": 1592170376,
"by": "6D85344C-660D-418E-9514-D248D558E7A8"
},
"name": "My Deployment",
"platform": {
"id": "123412341234",
"monitor": {
"ct_install_region": "us-east-1",
"enabled": true
},
"type": "aws"
},
"scan": true,
"scope": {
"exclude": [],
"include": [ {
"key": "/aws/us-east-1",
"policy": {
"id": "D12D5E67-166C-474F-87AA-6F86FC9FB9BC"
},
"type": "region"
}]
},
"status": {
"status": "ok",
"updated": 1592170376
},
"version": 1
}Deploy AWS protection automatically
In the previous step, an automatic mode deployment was created. Following creation, Alert Logic services will create all required resources using the third-party IAM role that was provided. An IDS and scan appliance will be installed on each VPC in us-east-1 that contains at least one running EC2 instance.