Update Azure RBAC Roles
This document is intended for Managed Detection and Response customers who need to review and adjust their credentials. Complete these instructions to ensure your environment is properly discovered.
Periodically, Alert Logic updates the policy corresponding to the RBAC roles required for Azure deployments. These updates, which Alert Logic announces in Alert Logic Console Release Notes, support new features and ensure your deployments continue to monitor your Azure assets.
Check for and fix Azure credential problems
The most common issue with Azure deployments is lack of credentials. For each of your Azure deployments, ensure that Role-Based Access Control (RBAC) is configured correctly with an app registration.
To check for credential issues:
- In the Alert Logic console, click the menu icon (
 ) to see the navigation menu.
) to see the navigation menu. - Click
 Configuration, and then click Deployments.
Configuration, and then click Deployments. - Click the relevant deployment tile, and then on the left navigation, under Access to Azure Subscription, click Azure Role.
- On the main pane, check the Active Directory ID and Application ID fields. If one or both fields are blank, you need to configure the app registration and RBAC for the deployment.
To fix this issue, see the instructions in Configure App Registration and RBAC for Microsoft Azure Resources.
Update the role document
You must replace the previous JSON file you saved when you first created an RBAC role.
- Create a new text file and copy the Alert Logic role into it. Note the directory where you save the file. You must know the path and file name for later.
- Make the following changes to the file:
- In the "Name": "<Resource Explorer (Alert Logic)>", line, change the <Resource Explorer (Alert Logic)> value? to the name of your app registration.
- In the "/subscriptions/<subscription id>" line, change the <subscription id> value to the subscription ID found in the Azure portal, on the Subscriptions blade.
- Save the text file as a JSON file.
Update the RBAC role document
You must update the custom RBAC role with the new path to the role document.
- Open either Azure CLI 2.0 or Azure PowerShell, log in to your Azure account, and then specify the default subscription.
 Azure Azure CLI 2.0 commands
Azure Azure CLI 2.0 commandsaz login
az account set --subscription <your subscription id>
 Azure Azure PowerShell commands
Azure Azure PowerShell commandsLogin-AzureRmAccount
Get-AzureRmSubscription –SubscriptionName <your subscription name> | Select-AzureRmSubscription
-
Update the following line with the new path.
 Azure Azure CLI 2.0 commands
Azure Azure CLI 2.0 commandsaz role definition create --role-definition <path to the role document>
 Azure Azure PowerShell commands
Azure Azure PowerShell commandsNew-AzureRmRoleDefinition -InputFile <path to the to the role document>
- In the Azure portal, under Subscriptions, select your subscription, and then click Access control (IAM).
- Click Roles to verify that the RBAC role you updated appears in the portal.
If the role does not appear, refresh the list of roles.
Troubleshoot permission errors
If you complete the configuration as described in Configure App Registration and RBAC for Microsoft Azure Resources, your Azure deployments should be ready to upgrade. You can optionally check for the following problems to prevent permission errors that can occur if your Azure deployment is not configured correctly.
Check for and fix permissions to access Microsoft Graph
To perform CIS benchmark checks, Alert Logic must have permission to access Microsoft Graph.
To check for permissions to access Microsoft Graph:
- In the Azure portal, click Azure Active Directory.
- On the left panel, click App registrations, and then select your app registration.
- On the left panel, click API permissions.
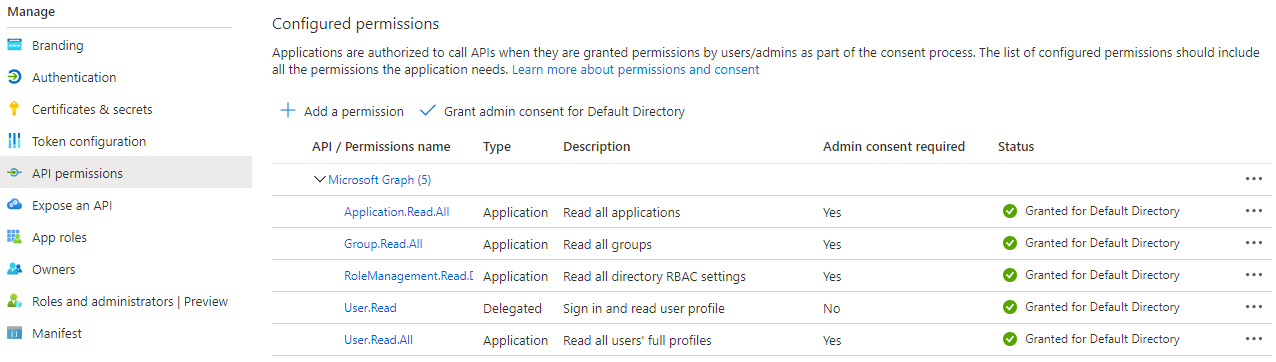
- Check that your configured permissions look like this:
If permissions are missing, you must grant them.
To grant permissions to access Microsoft Graph:
- On the API permissions page in the Azure console, click + Add a permission.
- On the Request API permissions blade, click Microsoft Graph.
- Click Application permissions, and then in the list, select the following permissions:
- Click Application to see permissions in this category, and then select Application.Read.All.
- Click Group to see permissions in this category, and then select Group.Read.All.
- Click RoleManagement to see permissions in this category, and then select RoleManagement.Read.Directory.
- Click User to see permissions in this category, and then select User.Read.All.
- Click Add permissions, and then on the API permissions pane, click Grant admin consent for Default Directory.
- In the pop-up window, click Yes to allow the changes you made on the permissions.
Check for and fix app registration role assignment
To prevent or fix permission errors, another item to check is that an RBAC role is assigned to your app registration.
The following procedures assume the RBAC role is created already, as described in Configure App Registration and RBAC for Microsoft Azure Resources.
To check that the role is assigned to the app registration:
- In the Azure portal, click Subscriptions.
- In the Subscriptions blade, select the subscription you want Alert Logic to protect, and then click Access control (IAM).
- Click the Role assignments tab.
- Check that the RBAC role you created is assigned to the app registration.
If a role is not assigned to your app registration, you must assign it.
To assign the role to the app registration:
- On the Role assignments tab in the Azure portal, click +Add, and then click Add role assignment.
- Select the RBAC role you created.
- From the list, click the app you registered earlier.
- Click SAVE.