Scan Host Summary
The Scan Host Summary report provides a breakdown of vulnerable hosts and vulnerability instances found by the selected scan with asset-level detail. Use this report to help prioritize remediation efforts.
To access the Scan Host Summary report:
- In the Alert Logic console, click the menu icon (
 ), and then click
), and then click  Validate.
Validate. - Click Reports, and then click Vulnerabilities.
- Under Scan Schedule Breakdown, click VIEW.
- Click Scan Host Summary.
View the latest scan report for a specific schedule
To view the report for the latest or most recent scan for a specific schedule, you must:
- Select a single value for the Customer Account, Deployment Name, and Scan Schedule Name filters.
- Select Show Latest Scan for the Scan Date Option to automatically set the Scan Start Date to Latest.
View a previous scan report for a specific schedule
To view the report for a previous scan for a specific schedule, you must:
- Select a single value for the Customer Account, Deployment Name, and Scan Schedule Name filters.
- Select Show All Available from the Scan Date Option filter.
- Select a single value from the Scan Start Date filter.
Filter the report
To refine your findings, filter your report by Category.
Filter the report using drop-down menus
By default, Alert Logic includes (All) values for most filters in the report.
To add or remove filter values:
- Click the drop-down menu in the filter, and then select or clear values.
- Click Apply.
Download the report
You can download the Scan Host Summary report as a CSV or PDF file. To learn how to download reports, see Report Download Option.
Schedule the report
After you finish setting up the report, you can use CREATE REPORT to run it periodically and subscribe users or an integration (such as a webhook) to receive a notification when the report is generated. To learn how to schedule the report and subscribe notification recipients, see Scheduled Reports and Notifications.
You can only schedule the Scan Details List report after you select Show Latest Scan for the Scan Date Option. This is required to ensure that a report is generated for the most recent scan and not the same scan on a recurring basis.
Scan result categories
If the selected deployment has agent-based scanning enabled, Alert Logic consolidates agent-based scan results with the latest available internal network scan to provide a complete vulnerability assessment. You can use the Category filter to isolate vulnerability assessments in consolidated results. Listed categories include the vulnerability scan type(s) associated with the selected schedule:
| Category | Vulnerability Scan Type |
|---|---|
| Agent | Agent-based scan |
| Credentials | Internal network scan with credentials (authenticated) |
| Network | Internal network scan without credentials (unauthenticated) |
| External | External network scan |
For information about each scan type, see About Alert Logic Scans.
CVSS scores and severity
Alert Logic assigns
| Severity rating | CVSS v2 score range | CVSS v3 score range |
|---|---|---|
|
|
Not applicable | 9.0 - 10.0 |
|
|
7.0 - 10.0 | 7.0 - 8.9 |
|
|
4.0 - 6.9 | 4.0 - 6.9 |
|
|
0.1 - 3.9 | 0.1 - 3.9 |
|
|
0.0 | 0.0 |
Some vulnerabilities in the National Vulnerability Database have both CVSS v2 and CVSS v3 scores. Alert Logic displays the newer CVSS v3 score and severity rating in prominent locations and both scores in detail views. If only one CVSS score exists, Alert Logic uses that score and severity rating.
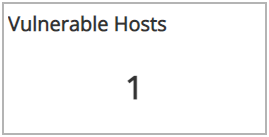
Vulnerable Hosts section
This section provides the total number of hosts with vulnerabilities found by the selected scan.
Vulnerability Instances section
This section provides the total number of vulnerability instances found by the selected scan.

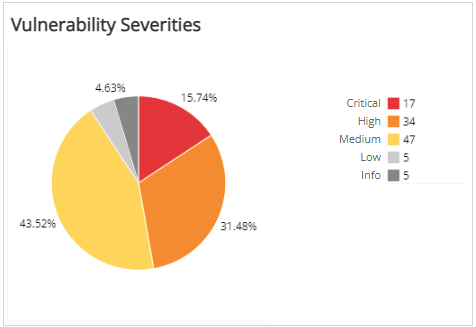
Vulnerability Severities section
This section provides the vulnerability count and percentages in each CVSS severity category found by the selected scan.
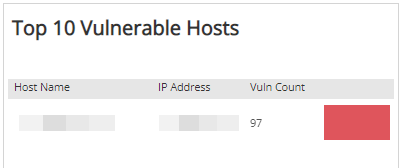
Top 10 Vulnerable Hosts by Vulnerability Count section
The list provides the top 10 vulnerable hosts by total vulnerability count found by the selected scan. The list is organized by host name, IP address, vulnerability count, and a bar graph that represents the relative count of vulnerabilities by IP address. Hover the bar graph to see the relative percentage of vulnerabilities for each IP address.
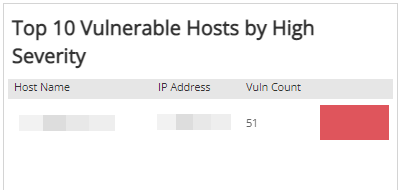
Top 10 Vulnerable Hosts by High Severity section
The list displays the current top 10 vulnerable hosts based on the count of critical and high severity vulnerabilities found by the selected scan. The list is organized by host name, IP address, critical and high severity vulnerability count, and a bar graph that represents the relative count of critical and high severity vulnerabilities by IP address. Hover the bar graph to see the relative percentage of critical and high severity vulnerabilities for each IP address.
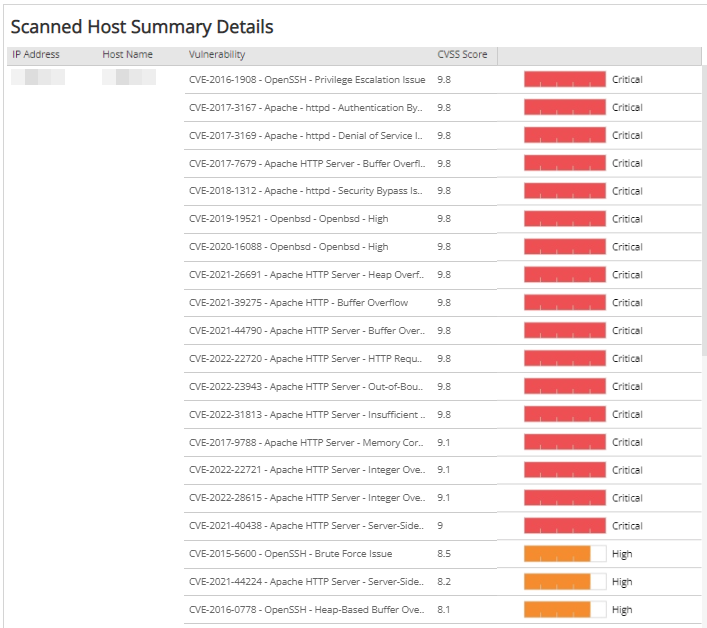
Scanned Host Summary Details section
The list provides the breakdown of vulnerable hosts by vulnerability severity found by the selected scan. The list is organized by IP address, host name, vulnerability, protocol/port, CVSS score, and the severity of the vulnerability. You can hover the severity bar to see a tooltip with additional details about the vulnerability.