List of Vulnerabilities
The List of Vulnerabilities report returns a tabular list of all current vulnerabilities and information about the assets affected by the vulnerability. Use this report to address and further analyze specific vulnerabilities and vulnerability instances found in your environment.
To access the List of Vulnerabilities report:
- In the Alert Logic console, click the menu icon (
 ), and then click
), and then click  Validate.
Validate. - Click Reports, and then click Vulnerabilities.
- Under Vulnerability List, click VIEW.
- Click List of Vulnerabilities.
Filter the report
To refine your findings, filter your report by Deployment Name, Disposed, Region, VPC/Network, Subnet, Security Groups, Asset Type, Category, Severity, and CVSS Score.
Filter the report using drop-down menus
By default, Alert Logic includes (All) values for most filters in the report.
To add or remove filter values:
- Click the drop-down menu in the filter, and then select or clear values.
- Click Apply.
The tabular list is organized by vulnerability name, category, CVSS Score, severity, deployment name, asset count, asset name, IP address, protocol, port and first seen.
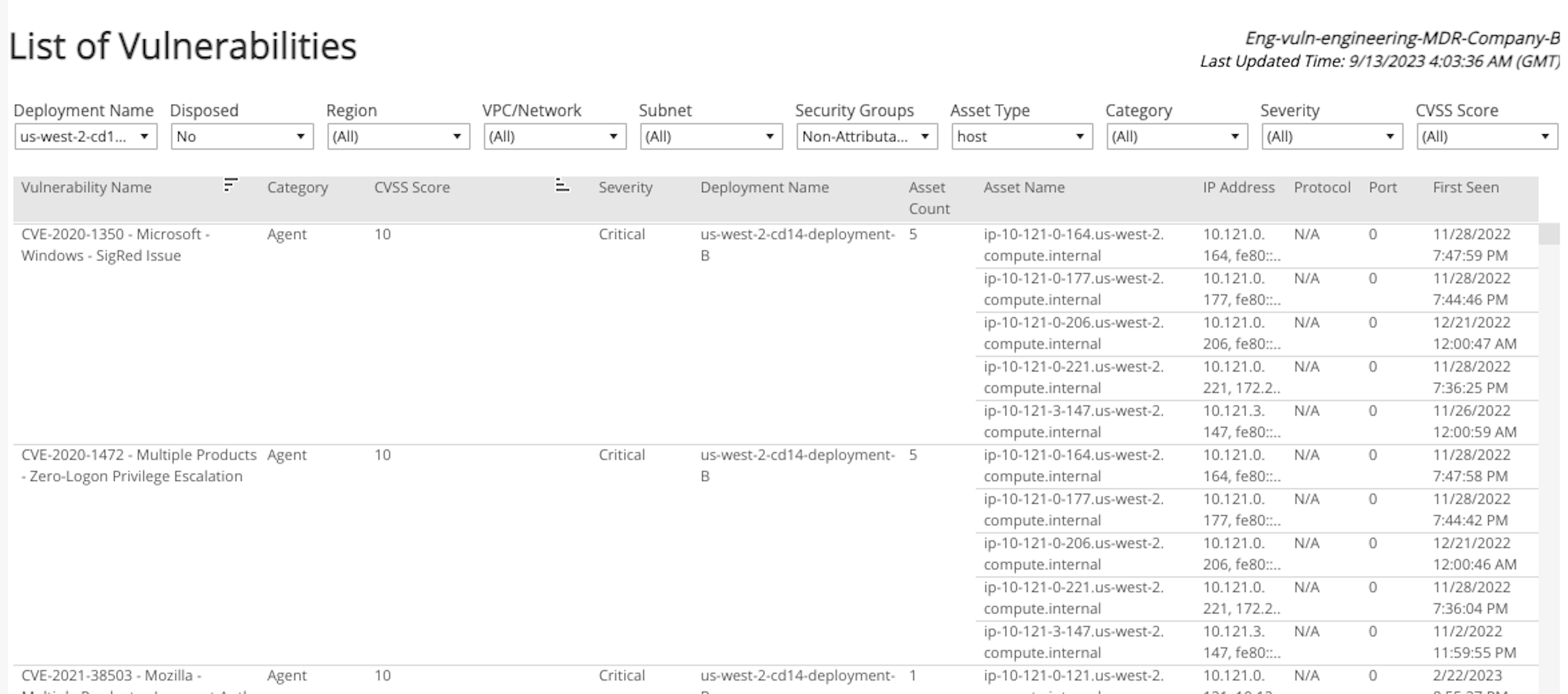
To see more information about the vulnerabilities in the list, you can set your filter preferences and download the full details for each vulnerability including evidence, age, impact, resolution, exposure assessment, and more.
To learn how to download reports, see Report Download.
Schedule the report
After you finish setting up the report, you can use CREATE REPORT to run it periodically and subscribe users or an integration (such as a webhook) to receive a notification when the report is generated. To learn how to schedule the report and subscribe notification recipients, see Scheduled Reports and Notifications.