Deployment with AWS Control Tower
Customers who use AWS Control Tower and Alert Logic can get automatic protection of existing and newly enrolled accounts through a series of automations.
Architecture
The Alert Logic Control Tower Automation uses the following AWS Services to enable automatic protection of newly added AWS Accounts:
- Amazon EventBridge
- AWS CloudFormation
- AWS Lambda
- Cross-account IAM Roles
- AWS Secrets Manager
- Amazon SNS
- Amazon SQS
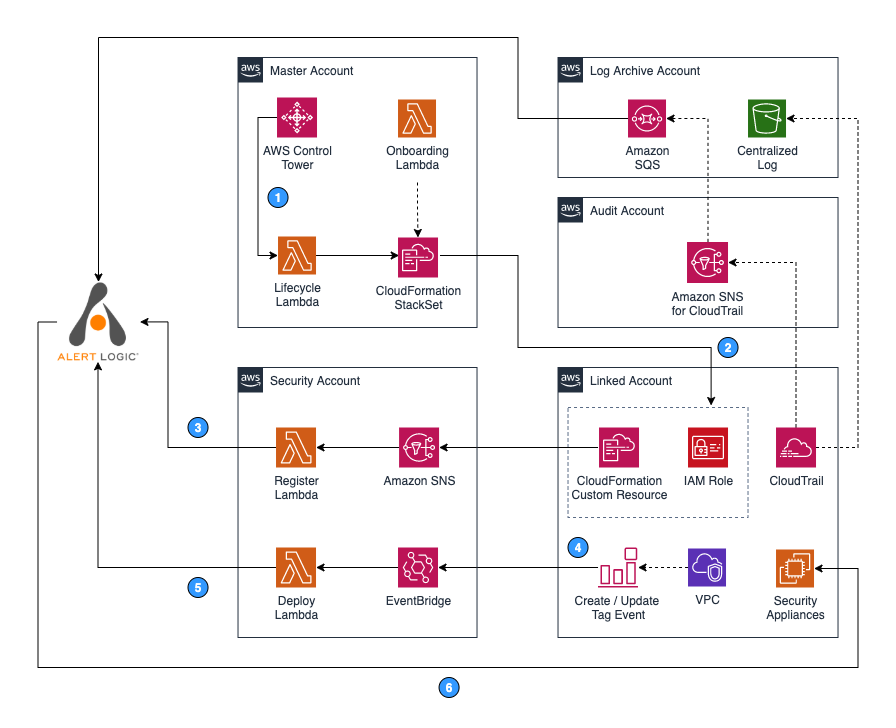
Accounts shown in the architecture diagram:
- Control Tower Management Account—Master account on which AWS Control Tower was enabled.
- Log Archive Account—Account for centralized repository of logs, including CloudTrail logs.
- Audit Account—Restricted account with read/write access to all accounts. A centralized CloudTrail SNS Topic for security and CloudTrail notification is located here.
- Security Account—An account where Alert Logic Control Tower Automation orchestration is deployed.
- Linked Account—One or more AWS accounts protected by Alert Logic. Alert Logic deploys appliances and agents into this account.
The following steps are associated with the numbers indicated in the architecture diagram.
- When a new Linked account is enrolled into AWS Control Tower, the LifeCycle lambda function receives a notification from AWS Control Tower and deploys an AlertLogic-CT StackSet Instance to the new Linked account.
- In the new Linked account, AlertLogic-CT StackSet Instance creates an IAM Role to enable Alert Logic Asset Discovery. Upon completion, the StackSet Instance sends an SNS event via Custom Resource to the Security account to notify that a new deployment must be registered with Alert Logic.
- In the Security account, a lambda function named Register is subscribed to the ALHubTopic SNS topic to receive new deployment registration requests from the new Linked account. Once the function receives a notification request, it registers a new linked account deployment with Alert Logic.
- When a user in the new Linked account tags or untags any VPCs, an event is published to Amazon EventBridge.
- A lambda function named Deployer receives the event and updates deployment protection scope in the Alert Logic console accordingly.
- If you specified Automatic mode during the initial setup, Alert Logic creates a security subnet in a newly protected VPC and deploys Alert Logic appliances. If you chose Manual mode, you must deploy the appliances to protect newly added VPCs. To learn more about deployment modes, see About Deployment Types.
Deployment begins with a CloudFormation stack deployed in the AWS Control Tower Master account. The stack creates two AWS Lambda Functions, two AWS CloudFormation StackSets, and an AWS CloudWatch Event Rule for AWS Control Tower Lifecycle. Onboarding Lambdas are used during initial deployment to orchestrate an AlertLogic-CT StackSet Instance, create an SQS in the Log archive account, and SQS to SNS subscription in the Audit account. Onboarding Lambda also orchestrates AlertLogic-CT-Central-IAM-Role stackset (not shown in the diagram) to create a StackSet Instance in the Log Archive account for CloudTrail ingestion. The CloudWatch Event Rule triggers the Lifecycle Lambda during new AWS account setup. This Lambda deploys AlertLogic-CT StackSets to the new AWS account.
The AlertLogic-CT StackSet launches stackset instances in all AWS accounts included in the scope of deployment. In each account, this stackset creates an IAM role for Alert Logic and a CloudWatch Event rule for detecting tag changes on VPC. The AlertLogic-CT stackset create additional resources in the Security Account, including an Amazon SNS Topic, two AWS Lambda Functions, and an Amazon EventBridge Event bus.
Prerequisites
- Create the Security Account prior to deploying this integration.
- In some cases, it is necessary to update the Service Quotas for Lambda concurrent executions in the Log Archive and Audit accounts for the the Control Tower home region. These limits can be validated in the 'Service Quotas' service and should be increased to at least 1000.
Deployment and Configuration
Deploy the CloudFormation stack
- Create an access key and a secret key in the Alert Logic console. For more information about how to create an access key and secret key, see Create and Manage Alert Logic Access Keys.
- Log in to the AWS Control Tower management account as a user with the AWSAdministratorAccess role or equivalent access.
- To deploy the solution, create a new CloudFormation Stack using this template.
- Provide the following information to deploy the CloudFormation Stack:
- Alert Logic Customer ID - On the Support page in the Alert Logic console
- Alert Logic API Access Key and Alert Logic API Secret Key - Key that was created in step 1
- Appliances deployment mode - Automatic will deploy appliances in all protected VPCs as accounts are set up. Manual mode requires appliances to be deployed in each VPC using additional cloud formation templates, but allows more flexibility.
- Security Account - AWS account created for Alert Logic integration above
- OUs to protect/exclude - By default, all enrolled AWS accounts are included in the Alert Logic integration. To specifically include or exclude OUs, enter the OU IDs as a comma separated list.
- Target Region - This should always be the home region that the Control Tower landing zone is deployed into. If this is anything other than us-east-1, the template URLs in the last half of the parameters will need to be updated to match.
- Control Tower Audit Account ID – Control Tower AWS audit account
- Log Archive Account ID - Control Tower log archive account
Verify linked accounts
After you complete the CloudFormation deployment, you can see your linked accounts listed as deployments in the Alert Logic console. This process typically takes around 10 to 15 minutes for all accounts to be included.
If the ‘Automatic’ deployment mode parameter is selected, the Alert Logic appliance deploys automatically within 15 minutes to each protected VPC in the linked accounts.
Update policies for CloudTrail collection if KMS is in use
If KMS is in use in the Control Tower landing zone, additional configuration is required to enable access to the encryption key.
- Get Role ARN for centralized collection role:
- In Cloud Formation, select StackSets and locate the ‘AlertLogic-CT’ stackset
- On the parameters page, the role ARN is the AlertLogicCentralizedRoleArn parameter
- Add policy to the KMS key
- In the Control Tower service, select the Landing Zone Settings page
- Select the Configurations page
- Scroll down and click on the KMS key id to open a new tab in KMS
- Add the following policy statement near the end of the key policy:
{
"Sid": "Allow alertlogic to decrypt log files",
"Effect": "Allow",
"Principal": {
"AWS": "[RoleARN]"
},
"Action": "kms:Decrypt",
"Resource": "*"
} Copy the KMS key ARN
- Update policy on log collection role
- Switch accounts to the Log Archive account
- In IAM, select roles and locate the log collection role (see RoleARN that was found in Cloud Formation in step 1 or search for ‘cix’)
- Add the following policy statement near the end of the inline policy:
{
"Sid": "AllowUseOfKeyInMaster",
"Effect": "Allow",
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "[KMS key ARN]"
}
Next Steps
Deploy appliances for manual mode
If the ‘Manual’ deployment mode is selected, appliances will need to be deployed as described in the AWS Deployment Professional documentation.
Deploy GuardDuty collector
It is normal to implement Guard Duty in a centralized manner, particularly in Control Tower environments. To integrate Guard Duty findings into the Alert Logic environment, the following documentation should be followed to deploy the collector in the Log Archive account and region: Integrate GuardDuty Findings