Configure AWS Network Firewall Log Collector
The Alert Logic Amazon Web Services (AWS) Network Firewall log collector is designed to collect AWS Network Firewall alerts delivered to an Amazon Simple Storage Service (S3) bucket. You can find AWS Network Firewall alerts collected with keyword search in the Alert Logic console Get Started with Search page. The message type is "AWS Network Firewall Alert." You can create correlations to generate incidents from these alerts. For more information, see Correlations and Notifications.
You must complete the following to successfully configure your AWS Network Firewall log collector:
- Set up an SNS topic and IAM role in your AWS account
- Set up S3 notifications in your AWS account
- Configure collection in the Alert Logic console
- Add Alert Logic firewall rules to your AWS Network Firewall policy
You can use the same setup in AWS for configuring the AWS Network Firewall log collector and the Amazon S3 log collector. If you have already completed the setup in AWS and want to reuse it, you can skip to Configure collection in the Alert Logic console.
Set up an SNS topic and IAM role in your AWS account
In the AWS account that hosts your S3 buckets, you must set up an Amazon Simple Notification Service (SNS) topic where AWS publishes S3 notifications. You must also set up an IAM role to grant Alert Logic access to your S3 buckets.
Use an AWS CloudFormation template that Alert Logic provides to set up the SNS topic and IAM role, or you can set them up manually.
Set up an SNS topic and IAM role with a CloudFormation template
Alert Logic recommends that you deploy the Alert Logic CloudFormation template to set up the SNS topic and IAM role.
To set up an SNS topic and IAM role with a CloudFormation template:
- Click the following link, and ensure you select the same region as your S3 bucket. Note this region identifier (for example, us-east-2 for Ohio), which you need when you configure the collector in the Alert Logic console.
- Under Parameters, in the External ID field, enter your Alert Logic Account ID.
- In the Stack Name and AlertLogicAWSAccountId fields, leave the default values.
- Select the I acknowledge that AWS CloudFormation might create IAM resources with custom names check box.
- Click Create stack to deploy the stack.
- View the stack output to retrieve the IAM Role ARN, SNS Topic ARN, and External ID, which you need when you configure the collector in the Alert Logic console.
Set up an SNS topic and IAM Role manually
If you are unable to use CloudFormation in your AWS account, you can use the following procedures instead to set up the SNS topic and IAM role manually.
Set up an SNS topic for S3 notifications manually
In the AWS account that Alert Logic protects, you must create an Amazon SNS topic to which Amazon S3 can publish notifications. The SNS topic must be in the same region as your S3 bucket.
You must also configure the SNS topic access policy to allow S3 to publish notifications to the topic and grant Alert Logic permission to receive and process S3 notifications, specifically object created events.
To set up an SNS topic for S3 notifications manually:
- Sign in to the Amazon SNS console.
- In the left navigation pane, choose Topics.
- Choose to create a Standard topic.
- Click this link to download the S3 SNS access policy document (JSON file). Keep the link open so you can edit the example as described next.
- In the Access policy section, click Advanced to use the downloaded example to configure the SNS topic access policy to allow S3 to publish notifications to the topic and grant Alert Logic permission to subscribe to updates.
The example allows the publishing of S3 notifications from S3 bucket "my-bucket" in AWS account 123456789101 to an SNS topic with ARN arn:aws:sns:us-east-2: 123456789101:my-sns-topic. It also grants Alert Logic permission to subscribe to the SNS topic. Edit the example as follows:
- Replace values for the SNS topic ARN in lines 15 and 32.

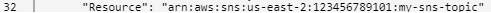
- Replace the AWS account in line 18.

- Replace the S3 bucket name in line 21.

Add the statements to your SNS access policy.
If you are using encrypted SNS, you will need to add the following two stanzas to your KMS key. The key must be multi-region and customer-managed to function correctly.Copy{
"Sid": "Allow Amazon SNS to use this key",
"Effect": "Allow",
"Principal": {
"Service": "sns.amazonaws.com"
},
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey*"
],
"Resource": "*"
},
{
"Sid": "Allow Amazon S3 to use this key",
"Effect": "Allow",
"Principal": {
"Service": "s3.amazonaws.com"
},
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey*"
],
"Resource": "*"
}
- Replace values for the SNS topic ARN in lines 15 and 32.
- Scroll to the end of the form and choose Create topic.
Set up an IAM role in AWS for your S3 buckets manually
Alert Logic uses AWS IAM role-based authentication to enable access to your S3 buckets. Before you configure your S3 collector in the Alert Logic console, you must first create an IAM role with the necessary permissions that Alert Logic can use to retrieve objects from S3.
To create an IAM role for your S3 buckets manually:
- In the AWS console, navigate to the IAM service.
- Navigate to Policies, and then click Create Policy.
- Click the JSON toggle to edit your permissions manually.
- Click this link to download the policy and paste the JSON into the text box.
Update the "Resource" lines in the JSON to include your bucket (see lines 21,22, and 31 in the box below):
Copy{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "S3RetrieveObjects",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucketMultipartUploads",
"s3:GetBucketTagging",
"s3:GetBucketLogging",
"s3:ListBucketVersions",
"s3:GetObjectTagging",
"s3:ListBucket",
"s3:GetBucketAcl",
"s3:GetBucketNotification",
"s3:GetBucketLocation",
"s3:ListMultipartUploadParts"
],
"Resource": [
"arn:aws:s3:::<YOUR BUCKET NAME>",
"arn:aws:s3:::<YOUR BUCKET NAME>/*"
]
},
{
"Sid": "S3ListBuckets",
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets"
],
"Resource": "arn:aws:s3:::<YOUR BUCKET NAME>"
}
]
}
- Click Next, and then enter a descriptive name for your policy.
- Click Create Policy.
- Under Roles, click Create Role.
- Under Select trusted entity, click AWS Account and then under the section that appears, select Another AWS Account.
- In the Account ID field, enter 230378978437.
- Under Options, select Require external ID, and enter an external ID of your choosing. Make note of it. You will need the value when you configure the collection in the Alert Logic console.
- Select the policy you created.
- Enter a Role name, and then click Create Role.
- Take note of the Role ARN value. You will need this value when you configure the collection in the Alert Logic console.
- In the Review Policy section, type a descriptive Policy name (for example, AlertLogicS3AccessPolicy).
- Return to your Role creation page, and then click the policy you created.
- Type a Role name, and then click Create Role.
- Note the Role ARN value, which you will need when you configure the collection in the Alert Logic console.
Set up S3 notifications in your AWS account
The next step is to send Amazon S3 notifications to the Amazon SNS topic you set up.
To set up S3 notifications:
- Log in to AWS and navigate to the Amazon S3 service console.
- Select the S3 bucket that collects the logs you want Alert Logic to process.
- In the Properties tab, scroll to the Event Notifications section.
- Click Create Event Notification.
- In the Name field, type a descriptive name for this event.
- (Optional) To limit the objects that Alert Logic receives notifications about, add the prefix in the Prefix field. Use this option if, for example, you store your logs in a particular folder.
- Leave the Suffix field blank.
- Select the All object create events check box.
- Under the Destination section, click SNS Topic.
- Select the SNS topic created in the previous procedure, and then click Save.
A message notifies you whether the event was created successfully, and if not, provides troubleshooting tips.
Configure collection in the Alert Logic console
After you set up the SNS topic, IAM role for your S3 buckets, and S3 event notifications in AWS, you must complete the next step of the collection configuration process in the Alert Logic console. This configuration is an account-level integration, which means you can configure more than one instance of AWS Network Firewall log collection. This capability is useful when more than one instance of the application exists.
To access the Application Registry page, click the menu icon (![]() ). Click
). Click ![]() Configure, and then click Application Registry.
Configure, and then click Application Registry.
To add a new application collection:
- In the Application Registry, click the AWS tile, and then click AWS Network Firewall.
- In the Application Name field, enter a name for this AWS Network Firewall collection instance.
- Under Collection Method and Policy, in the Role ARN field, enter the ARN for the IAM role granting access to your S3 bucket that you noted earlier.
- In the External ID field, enter the value in the External ID field that you noted earlier.
- In the S3 Bucket Name field, enter the name of the S3 bucket from which to collect alerts.
- (Optional) If you want Alert Logic to collect logs from a particular folder in your S3 bucket, in the S3 Object Key Prefix field enter the prefix that identifies the folder, followed by a slash (for example, "logs/"). Leave this field blank if you want Alert Logic to collect all objects in the bucket.
- In the SNS Topic ARN field, enter the ARN of the SNS topic created earlier that receives S3 notifications (for example, arn:aws:sns:us-east-2: 123456789101:my-sns-topic).
- In the SNS Topic Region field, select the AWS region where S3 sends notifications when data is stored in S3.
- Under Firewall Rules, click DOWNLOAD THE RULES. You need these Alert Logic IPS rules to finish the integration in the next procedure.
- Click ADD. Wait a few minutes for the application to create and appear in your application list. Do not click ADD again.
The Health console also indicates whether the application collector is healthy or unhealthy. For more information, see Health.
Add Alert Logic firewall rules to your AWS Network Firewall policy
Alert Logic provides stateful firewall rules compatible with Suricata and Snort open source IPS rule specifications. For full integration with Alert Logic, you must download the Alert Logic firewall rules (see Configure collection in the Alert Logic console), create a firewall rule group in AWS with the Alert Logic rules, and then add the rule group to your firewall policy.
The following procedure explains how to complete the process in the AWS console, but you can use AWS APIs instead.
If you load the rules into your network firewall policy and an event occurs that matches a rule, AWS produces a message that Alert Logic collects. Alert Logic also collects events that you configure with other rules.
To add Alert Logic firewall rules to your firewall policy:
- In the AWS console, browse to the VPC page.
- In the navigation pane on the left, click Firewalls.
- Follow instructions on the page to create the firewall to which you want to add Alert Logic IPS rules or select an existing firewall.
- In the Stateful rule groups section, click Add rule groups, and then select Create and add new stateful rule group.
- Enter details about the stateful rule group, and under Choose how you want to configure the stateful rules, select Suricata compatible IPS rules.
- Under Suricata compatible IPS rules, select Enter Suricata compatible IPS rules, and then paste the contents of the file you downloaded in the previous procedure in the field provided.
- Under Action, select Alert.
- Follow AWS instructions to associate the Alert Logic rule group you created with the firewall policy.