Agent-Based Scanning
Agent-based scanning enables users to leverage the vulnerability assessment coverage of authenticated network scanning without the need to manage credentials and with a reduction in network traffic and impact.
Upgrades to the scanning experience
The agent-based scan upgrade improves the efficiency, accuracy, and usability of Alert Logic vulnerability scanning features.
No credential management
Agent-based scanning does not require credential management. Users of authenticated network scans had to configure access and manage credentials for assets and networks. The agent is installed on the host and does not require any further credential management to maintain.
Reduced network traffic
Agent-based scanning reduces network traffic by running locally on the host before sending results to Alert Logic for final analysis.
Limited network and host processing impact
Agent-based scanning reduces network impacts by running locally on the host and limits host processing impact to less than 5 minutes. For detailed information on host impacts, see Requirements for the Alert Logic agent with scan components.
Increased host-target availability
You can deploy the agent on hosts that are impossible or impractical to scan from the network. Agent-based scanning makes it possible to protect even hardened systems that prevent network scanning, hosts on low bandwidth networks, and transient hosts such as laptops.
Better vulnerability accuracy
Agent-based scanning increases the accuracy and reliability of vulnerability scan results. Improved coverage includes better operating system, application, patch, and kernel level vulnerability assessment.
No redundant vulnerability assessment
Agent-based scans and credentialed network scans provide similar vulnerability assessment coverage for operating system, application, patch, and kernel level vulnerabilities. To reduce impact to the network and host, when a network scan begins scanning a particular host, it checks in with that host for the presence of agent-based scan configuration.
If agent-based scan is configured on the host:
The agent will evaluate operating system, application, patch, and kernel vulnerabilities. The network scan will not run redundant vulnerability assessments for the host.
If agent-based scan is not configured on the host:
The network scan runs vulnerability assessments as configured (with or without credentials) against the host. The credentialed network scan will evaluate vulnerabilities for configuration checks, web applications testing, and active exploit, SQL injection, and so on.
Requirements
A host must meet the following criteria to support agent-based scanning.
Node subscription level
The host node must be configured for Alert Logic MDR Essentials, Alert Logic MDR Professional, or Alert Logic MDR Enterprise level of protection. You can verify or change the protection levels by using Entitlement Summary or Change Protection Level of an Asset.
Host operating system
The host must run a supported Windows or Linux operating system.
The agent-based scanning components are supported on the following operating systems. Older Linux and Windows operating systems may work, but they will report a large amount of vulnerabilities.
| Operating System | Versions | Installation Guide |
|---|---|---|
| Amazon Linux | 1.x, 2.x | Install the Alert Logic Agent for Linux |
| CentOS | 6.x, 7.x, 8.x | Install the Alert Logic Agent for Linux |
| Red Hat Enterprise Linux (RHEL) |
6.x, 7.x, 8.x |
Install the Alert Logic Agent for Linux |
| Ubuntu | 16.x, 18.x, 20.x | Install the Alert Logic Agent for Linux |
| Windows 7 | All | Install the Alert Logic Agent for Windows |
| Windows 8 | All | Install the Alert Logic Agent for Windows |
| Windows 10 | All | Install the Alert Logic Agent for Windows |
| Windows Server 2008 | All | Install the Alert Logic Agent for Windows |
| Windows Server 2012 | All | Install the Alert Logic Agent for Windows |
| Windows Server 2016 | All | Install the Alert Logic Agent for Windows |
| Windows Server 2019 | All | Install the Alert Logic Agent for Windows |
Agent-based scanning health
The agent must be installed on the host. The health status of the agent related to connectivity or resource issues may affect the installation and execution of agent-based scanning. You can verify the health status and presence of an agent on a specific host by using the Health page, the Missing Agent Digest report, and the Agent view on the Topology page.
If you need to increase the frequency of agent-based scans or exclude hosts with an unsupported operating system, Alert Logic also reports a Scan category exposure on the Health page.
Requirements for the Alert Logic agent with scan components
Scan components of the agent require the following in addition to the standard Requirements for the Alert Logic Agent.
| Requirement Type | Additional System Requirement for Scan Components | Total System Requirement (Agent + Scan Components) |
|---|---|---|
| Storage | 102MB | 652MB |
Processing requirements and host impact for running an agent-based scan
The agent-based scan runs at a different time than the network scan, though if you choose to use internal network scan schedules for agent-based scans the results are not enumerated and delivered until a network scan is complete with the host in scope. The host impact for processing requirements only occurs for the duration defined below, at run-time.
| Type | Operating Systems | Scan Components | System Requirement | Duration of Demand (Estimate) |
|---|---|---|---|---|
| RAM (Max) | Windows | OSQuery | 50MB | 5 seconds |
| OVALdi | 70MB | 3 minutes | ||
| Linux | OSQuery | 30-70MB | 5 seconds | |
| OVALdi | 90MB | 4 minutes | ||
| CPU | Windows | Both | Up to 100%, running at low priority | 3-4 minutes |
| Linux | Both | Up to 100%, running at low priority | 4-5 minutes |
How to enable or disable agent-based scanning
Agent-based scanning is enabled and disabled by deployment. By default, agent-based scanning is disabled on all deployments. Once enabled, current and future agents will automatically install the new scan components as an update following Agent or remote collector outbound rules (US) or Agent or remote collector outbound rules (UK).
To enable agent-based scanning for an existing deployment:
- In the Alert Logic console, click the menu icon (
 ) to see the navigation menu.
) to see the navigation menu. - Click
 Configure, and then click Deployments.
Configure, and then click Deployments. - Find the deployment you want to edit, and then click EDIT.
- In the left navigation panel, click Agent-Based Scanning.
- Select Enable agent-based scanning (recommended).
- Click SAVE.
- In the confirmation window, click ENABLE.
To disable agent-based scanning for an existing deployment:
- In the Alert Logic console, click the menu icon (
 ) to see the navigation menu.
) to see the navigation menu. - Click
 Configure, and then click Deployments.
Configure, and then click Deployments. - Find the deployment you want to edit, and then click EDIT.
- In the left navigation panel, click Agent-Based Scanning.
- Select Disable agent-based scanning (default).
- Click SAVE.
- In the confirmation window, click DISABLE.
Scan using the Alert Logic agent
An internal scan of a host that meets the Requirements for agent-based scanning will optimize vulnerability assessment.
Methods to schedule agent-based scans include:
Use agent-based scan schedules
Because of the default schedule, the initial agent-based scan runs within 12 hours after the install of the scan components on the host. If you choose to use custom agent-based scan schedules, scan windows defined in the agent-based scan schedules govern agent-based scans.
To use agent-based scan schedules:
- In the Alert Logic console, click the menu icon (
 ) to see the navigation menu.
) to see the navigation menu. - Click
 Configure, and then click Deployments.
Configure, and then click Deployments. - Find the deployment you want to edit, and then click EDIT.
- In the left navigation panel, click Scan Schedules.
- On the Agent-Based Scans page, ensure Use internal network scan schedules is turned off.
If the scan frequency is set to scan as often as necessary and the scan window is set to scan any time (default):
The agent-based scan runs at every 12-hour interval from the initial execution. The results of the agent-based host scan are visible in the Alert Logic console once the scan completes.
If the scan window is defined to specific start and end times:
The agent-based scan runs at the start of the window. The results of the agent-based host scan are visible in the Alert Logic console once the scan completes for the window. For more information on asset scopes in scan schedules, see Define the scope of the assets to scan.
Use internal network scan schedules
If you choose to use internal network scan schedules for agent-based scans, the scan windows defined in internal network scan schedules govern agent-based scan run-times.
To use internal network scan schedules for agent-based scans:
- In the Alert Logic console, click the menu icon (
 ) to see the navigation menu.
) to see the navigation menu. - Click
 Configure, and then click Deployments.
Configure, and then click Deployments. - Find the deployment you want to edit, and then click EDIT.
- In the left navigation panel, click Scan Schedules.
- On the Agent-Based Scans page, turn on Use internal network scan schedules.
If the scan frequency is set to scan as often as necessary and the scan window is set to scan any time (default):
The agent-based scan runs at every 12-hour interval from the initial execution. The consolidated results of the agent-based host scan are visible in the Alert Logic console once an internal network scan completes.
If the scan window is defined to specific start and end times:
The agent-based scan runs at the start of the window. The consolidated results of the agent-based host scan are visible in the Alert Logic console once the internal network scan completes for the window. For more information on asset scopes in scan schedules, see Define the scope of the assets to scan.
Use Scan Now
If you need to run a scan on a specific host immediately, you can use the Scan Now feature on the Topology page. This feature scans the selected host right away or as soon as possible, outside the normal schedule.
To see which internal network scans are in progress, click the scan icon () to see the scan statuses of your assets. For more information about scan status, see Customize the diagram display.
To use the Scan Now feature:
- On the Topology page, specify a deployment or region in the respective drop-down menus.
- Click the host you want to scan immediately, if a scan is not in progress.
- In the panel that opens, click the Actions tab, and then click SCAN NOW.
If the host is excluded from scanning in the deployment scope of protection, a message prompts you to confirm whether to continue with the scan. If ports are excluded, a message prompts you to choose whether to honor or override the exclusions. If you choose to honor exclusions, the scanner does not scan the excluded ports.
- Click OK to run the scan.
Scan Now prompts Alert Logic to scan the host as soon as possible. Depending on technological factors such as the current load on the scanner and the availability of a scan appliance, a delay of up to 25 minutes may occur before the internal network scan begins.
Exclude assets from agent-based scans
You can exclude deployment assets from agent-based scans. By setting exclusions globally, you can avoid managing them in each agent-based scan schedule. Excluding an asset from scans prevents future scans of the assets, but does not stop scans in progress. Exposures from previous scans are still reflected on the excluded assets.
To exclude assets or AWS tags from agent-based scans:
- Access the deployment for which you want to configure exclusions, and then click Scan Exclusions in the left navigation panel.
- Select the Agent-Based Scans tab.If you chose to use internal network scan schedules for agent-based scans, choose the Internal Network Scans tab instead.
- To exclude assets, click ASSETS to search for available assets to exclude, and then click EXCLUDE for the asset you want to exclude.
- (AWS deployments only) To exclude assets by using AWS tags, click TAGS to search for available tags to exclude, and then click EXCLUDE for the tag you want to exclude.
- On the Scan Exclusions page, click SAVE EXCLUSIONS.
View the results of an agent-based scan
Agent-based scan results are consolidated with latest internal network scan results, if available. Only agent-based scan results are posted if internal network scans are not configured or if internal network scan results are expired (more than 100 days old). If you choose to use internal network scan schedules for your agent-based scans, results are made visible when an internal network scan is completed. The consolidated results from agent-based and internal network scans are found on the Exposures page, and you can use the "Agent" category filter to isolate vulnerabilities detected by agent-based scans.
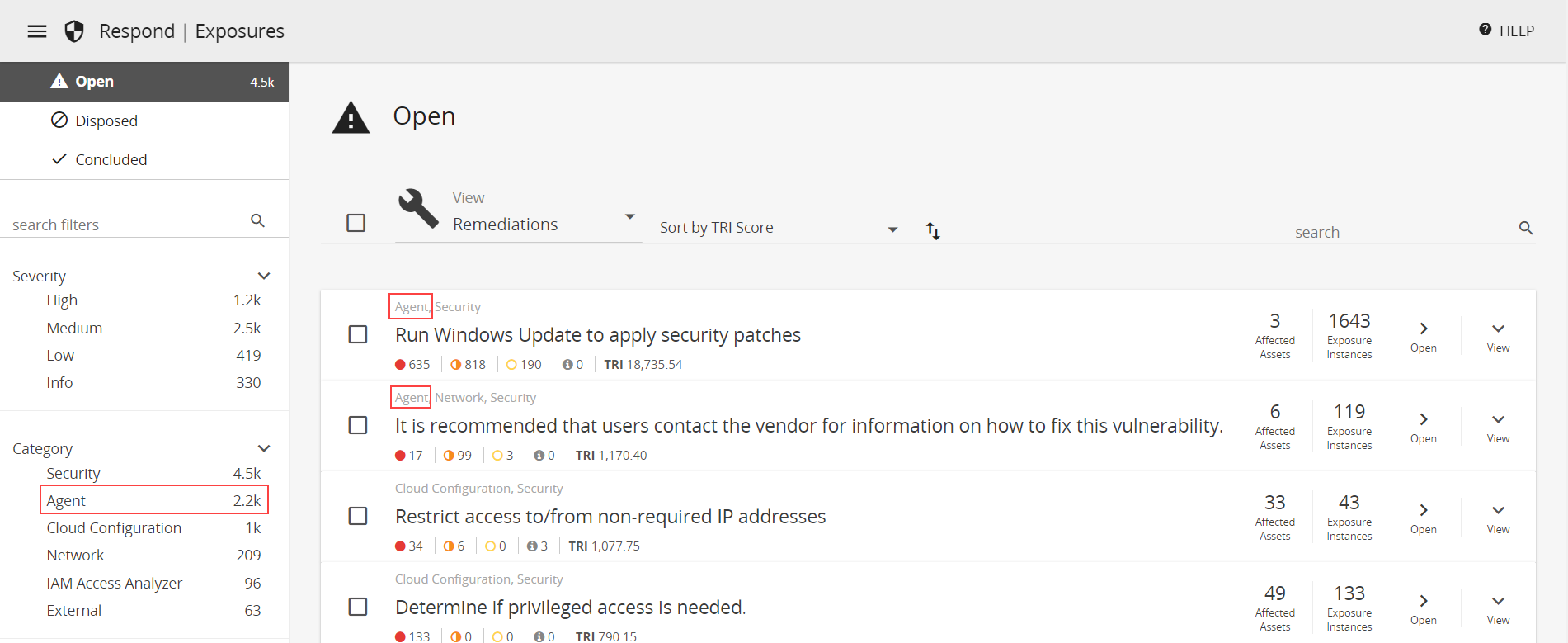
Agent-based scan results are also available in Vulnerabilities Reports and Remediations Reports.
Scan-based vulnerability assessment coverage details
Agent-based scans detect vulnerabilities and missing patches on hosts with an agent installed. For the most comprehensive vulnerability assessment coverage, you must also schedule internal network scans to run configuration checks (such as for missing TLS certificates and use of default account passwords) and conduct standard web application testing. See Manage Vulnerability Scan Schedules for details about scheduling internal network scans. Agent-based host scanning alone cannot be used for PCI compliance. See Manage PCI Scans for details.